Difference between revisions of "Benchmark dataset for training/testing of Machine Learning Models to detect cyber-attacks to an indoor real time localization system for autonomous robots"
(→Validation route ===) |
WikiSheriff (talk | contribs) |
||
| (One intermediate revision by one other user not shown) | |||
| Line 1: | Line 1: | ||
| + | <blockquote style="background-color:#ffe;border:1px solid #fb0;padding:5px 10px">SciCrunch! reference: '''Machine learning models cyber-attack detection Benchmark Dataset, RRID:SCR_015757.'''</blockquote> | ||
| + | |||
This data report summarizes a benchmark dataset which can be used to train and test Machine Learning Models to detect cyber-attacks to an indoor real time localization system for autonomous robots. Data have been gathered in an indoor mock-up apartment, shown in Fig 2, located at the Robotics Lab of the University of León (Spain). An autonomous robot, called Orbi-One and shown in Fig 1, with an on-board Real Time Location System (RTLS) was used to gather the data. | This data report summarizes a benchmark dataset which can be used to train and test Machine Learning Models to detect cyber-attacks to an indoor real time localization system for autonomous robots. Data have been gathered in an indoor mock-up apartment, shown in Fig 2, located at the Robotics Lab of the University of León (Spain). An autonomous robot, called Orbi-One and shown in Fig 1, with an on-board Real Time Location System (RTLS) was used to gather the data. | ||
| + | |||
| + | [[File:Logo_feder.png|thumb|300px]] | ||
| + | [[File:MICINN_Gob_Web_AEI.jpg|thumb|300px]] | ||
== Materials == | == Materials == | ||
Latest revision as of 10:06, 9 March 2022
SciCrunch! reference: Machine learning models cyber-attack detection Benchmark Dataset, RRID:SCR_015757.
This data report summarizes a benchmark dataset which can be used to train and test Machine Learning Models to detect cyber-attacks to an indoor real time localization system for autonomous robots. Data have been gathered in an indoor mock-up apartment, shown in Fig 2, located at the Robotics Lab of the University of León (Spain). An autonomous robot, called Orbi-One and shown in Fig 1, with an on-board Real Time Location System (RTLS) was used to gather the data.
Contents
Materials
Data gathered by Orbi-One robot include:
- Orbi-One location estimates provided by a commercial RTLS, called KIO.
Additional information about Karen and the devices/packages used to get data is given below.
Orbi-One robot
Orbi-One, shown at Fig 1, is an assistant robot manufactured by Robotnik. The software to control the robot hardware is based on ROS.
KIO RTLS
KIO RTLS commercial solution by Eliko has been used to provide people location at the study area. Fig 1 shows a KIO beacon (1), and a KIO tag on the robot (2).
Recording procedure
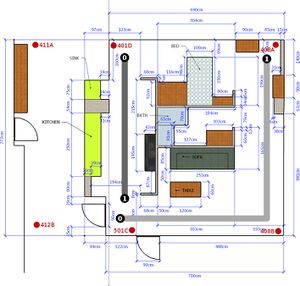
Two predefined trajectories were set for the robot in the study area, as shown in Fig 2: a test trajectory (light gray line in Fig 2) was used to build a training dataset, for training and testing the models; and a validation trajectory (dark gray line in Fig 2) was used to generate a different dataset to validate models in a different location ensuring generalization. The robot started in both cases at the point marked "0" and finished at the point marked "1"". Data were recorded by the Orby-One robot moving through the apartment, remotely controlled, following the test and validation trajectories respectively. We created a different rosbag file every time Orby-One made the walk, saving the location estimates gathered by the KIO device for a later analysis.
We repeated the test and validation trajectories 10 times each, so that 20 rosbag files were recorded. Orby-One takes about 72 seconds to finish the walk following the test trajectory, and about 40 seconds following the validation trajectory. Each test run yielded 270 location estimates on average, validation runs 150.
The runs were recorded in three different scenarios: without suffering any attack (labeled as WA), suffering a DoS attack (labeled as A1), and suffering a Spoofing attack (labeled as A2). DoS attacks were carried out by interrupting the signal of one or more radio beacons. Spoofing attacks were carried out by changing the signal of the radio beacons. The affected radio beacons were selected by looking for anchors with redundancy (A-anchors) and anchors without (C- and D-anchors), at different locations.
Data
v1.0
Without attack (WA)
Test route
- WA_2017-03-06-17-48-50.bag
- WA_2017-03-07-08-46-41.bag
- WA_2017-03-07-08-48-56.bag
- WA_2017-03-07-08-50-50.bag
- WA_2017-03-07-14-53-42.bag
- WA_2017-03-07-14-55-29.bag
Validation route
- WA-validation_2017-03-06-18-05-27.bag
- WA-validation_2017-03-07-08-53-28.bag
- WA-validation_2017-03-07-08-54-40.bag
- WA-validation_2017-03-07-08-55-48.bag
DoS attack (A1)
Test route
- A1-401d_2017-03-07-14-15-12.bag
- A1-408a_2017-03-06-17-53-12.bag
- A1-408b_2017-03-07-14-08-25.bag
- A1-501c_2017-03-07-09-00-44.bag
Validation route
- A1-401d-validation_2017-03-07-09-32-49.bag
- A1-408a-validation_2017-03-06-18-03-44.bag
- A1-408b-validation_2017-03-07-14-10-42.bag
- A1-501c-validation_2017-03-07-09-04-18.bag